
Ghidra is the most advanced reverse engineering tool on the market, and best of all it is completely free and open source! Most of the content on RetroReversing will be using Ghidra going forward due to it being much more accessible than competitors such as IDA Pro.
There is no better way to start out the hobby reverse engineering than learning Ghidra, it is an essential tool that takes much of the headaches out of reversing.
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github
An excellent guide for decompiling GBA games using Ghidra and mGBA is available on Starcubelabs
Another excellent guide is on wrongbaud
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github
It even has multiple builds setup for each Ghidra version via Github Workflows!
Note that there was another older Ghidra plugin called Ghidra-Nes-Rom-Decompiler-Plugin however it failed to build against latest Ghidra (11.1.2).
There is only one Ghidra plugin for SNES but it is currently not under active development you can get it from Github
Nintendo 64 games can be slightly harder to reverse due to everything being bundles as one large ROM image containing all the code and assets used in the game. Luckily there are a few tools that can help, such as the Reversing Emulator and a N64 Loader for Ghidra.
Download the Ghidra plugin from Github
Note that to build the GameCubeLoader you will need to have gradle version 7 or below installed otherwise you will get an error similar to:
FAILURE: Build failed with an exception.
* Where:
Build file './Ghidra-GameCube-Loader/build.gradle' line: 63
* What went wrong:
A problem occurred evaluating root project 'GameCubeLoader'.
> Adding a Configuration as a dependency is no longer allowed as of Gradle 8.0.
On Mac OSX you can install an older version of Gradle using brew:
brew install gradle@7
A guide for using Ghidra on Wii games is available on WiiBrew
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github Also for GDI support in Ghidra: Github
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github
Download the Ghidra plugin from Github Also for a guide for using Ghidra for PS1 reversing: tokimeki-memorial
Download the Ghidra plugin from Github
There are a few useful script for working with PS3 executables on Github
bordplate provides an in-depth introduction to using Ghidra for game reverse engineering, demonstrating the process by adding multiplayer to the PS3 port of Ratchet & Clank.
The video covers setting up Ghidra for PowerPC architecture, identifying game functions like spawnMoby through string analysis, and injecting custom C++ code to hook game logic and implement networking.
Download the Ghidra plugin from Github
While Ghidra has a large number of features built in, there are a number of features missing that are thankfully available due to community plugins, this section will cover some of the most useful for game reversing.
CodeCut allows a user to assign functions to object files in Ghidra, and then interact with the binary at the object file level. Functions are assigned to object files by setting the Namespace field in the Ghidra database. DeepCut attempts to establish initial object file boundaries which the user can then adjust using the CodeCut Table window. https://github.com/jhuapl/codecut
GhidrAssist is a powerful extension that integrates Large Language Models (LLMs) directly into the Ghidra reverse engineering workflow. The tool supports both local and cloud-based AI providers (such as OpenAI and Ollama) to facilitate tasks like code explanation, refactoring, and vulnerability detection. Uniquely, it features an ‘Agentic Mode’ utilizing the ReAct pattern, allowing the AI to autonomously plan and execute investigation steps within the binary.
WHen using the decompiler Ghidra spits out code which uses a number of macros which are not immediately obvious of their function, we provide some of these below with our recommendation of an easier to read version.
In Ghidra, the CONCAT11(x, y) operation combines two 8-bit values (x and y) into a single 16-bit value. The operation is defined as:
#define CONCAT11(x, y) = (((uint16_t)x) << 8) | ((uint8_t)y)
When cleaning up the decompiled code we suggest using the following replacement as it is more explicit about the purpose:
// MergeBytesTo16Bit - combines high and low bytes into a single 16bit value
#define MergeBytesTo16Bit(highByte, lowByte) = (((uint16_t)highByte) << 8) | ((uint8_t)lowByte)
Ghidra is the most advanced reverse engineering tool on the market, and best of all it is completely free and open source! Most of the content on RetroReversing will be... ...

Introduction This tutorial series will guide you through the basics of decompiling a C++ executable, from setup all the way to reversing C++ classes. The video tutorial is created by... ...
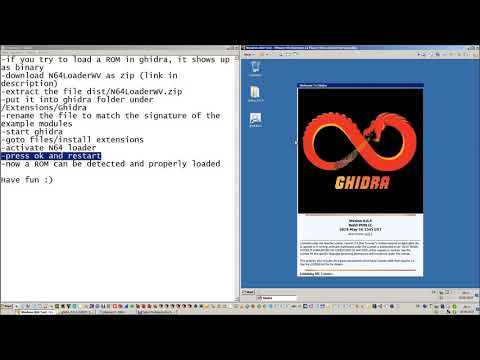
Importing a Nintendo 64 ROM Download and Install Ghidra Before following the steps on this post please make sure you have a working Ghidra environment setup. So you should be... ...
Introduction This page walks you through using Ghidra to reverse engineer NES ROMs using the Ghidra-Nes-Rom-Decompiler-Plugin. This plugin currently only supports a handful of the most common mappers but it... ...